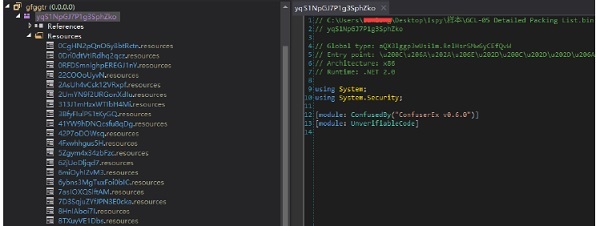
]1 加密混淆代码
使用 windbg 尝试进行脱壳,第一步定位解密后加载到内存中的可执行模块,通过调试分析发现程序运行后内存中会加载 stub 模块;
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
0:000> !CLRStack
PDB symbol for mscorwks.dll not loaded
OS Thread Id: 0xa68 (0)
ESP EIP
003ae488 773eb727 [HelperMethodFrame: 003ae488]
003ae52c 6e4b8496 System.IO.Path.CheckInvalidPathChars(System.String)*** WARNING: Unable to verify
checksum for
C:\Windows\assembly\NativeImages_v2.0.50727_32\mscorlib\62a0b3e4b40ec0e8c5cfaa0c8848e64a\m
scorlib.ni.dll
003ae538 6dd92736 System.IO.Path.NormalizePathFast(System.String, Boolean)
003ae5bc 6dd926c5 System.IO.Path.NormalizePath(System.String, Boolean)
@NSFOCUS 2016 http://www.nsfocus.com
003ae5cc 6dd92686 System.IO.Path.GetFullPathInternal(System.String)
003ae5d8 6dd39448 System.Reflection.Module.get_FullyQualifiedName()
003ae608 00626996 <Module>. )(
003ae694 00626739 <Module>..cctor()
003ae8a4 6e671b4c [GCFrame: 003ae8a4]
003aef8c 6e671b4c [GCFrame: 003aef8c]
003af170 6e671b4c [HelperMethodFrame_1OBJ: 003af170]
System.RuntimeMethodHandle._InvokeMethodFast(System.Object, System.Object[],
System.SignatureStruct ByRef, System.Reflection.MethodAttributes, System.RuntimeTypeHandle)
003af1e0 6dd85458 System.RuntimeMethodHandle.InvokeMethodFast(System.Object, System.Object[],
System.Signature, System.Reflection.MethodAttributes, System.RuntimeTypeHandle)
003af230 6dd85206 System.Reflection.RuntimeMethodInfo.Invoke(System.Object,
System.Reflection.BindingFlags, System.Reflection.Binder, System.Object[],
System.Globalization.CultureInfo, Boolean)
003af26c 6dd850ee System.Reflection.RuntimeMethodInfo.Invoke(System.Object,
System.Reflection.BindingFlags, System.Reflection.Binder, System.Object[],
System.Globalization.CultureInfo)
003af28c 006266f7 . (System.Reflection.MethodInfo, System.String[], Boolean)
003af2a8 00624512 . (System.String[])
003af504 6e671b4c [GCFrame: 003af504]
|
定位查看stub模块信息,发现其为完整PE文件,dump完整PE文件;
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
0:000> !Name2EE *!stub
Module: 6db71000 (mscorlib.dll)
———————————————————
Module: 00262360 (sortkey.nlp)
———————————————————
Module: 00262010 (sorttbls.nlp)
———————————————————
Module: 002626b0 (prcp.nlp)
———————————————————
Module: 00262a00 (mscorlib.resources.dll)
———————————————————
Module: 001c2ff8 (GCL–05 Detailed Packing List.exe)
———————————————————
Module: 6c661000 (System.Windows.Forms.dll)
———————————————————
Module: 6d3d1000 (System.dll)
———————————————————
Module: 6d241000 (System.Drawing.dll)
———————————————————
Module: 001c71c0 (stub, Version=0.0.0.0, Culture=neutral, PublicKeyToken=null)
0:000> !DumpModule 001c71c0
Name: stub, Version=0.0.0.0, Culture=neutral, PublicKeyToken=null
@NSFOCUS 2016 http://www.nsfocus.com
Attributes: PEFile
Assembly: 00494878
LoaderHeap: 00000000
TypeDefToMethodTableMap: 00a03de8
TypeRefToMethodTableMap: 00a03ef8
MethodDefToDescMap: 00a04090
FieldDefToDescMap: 00a04688
MemberRefToDescMap: 00a04b14
FileReferencesMap: 00a04e50
AssemblyReferencesMap: 00a04e54
MetaData start address: 005f53ec (97120 bytes)
|
查看 stub.exe 代码,发现其代码已经进行了解密,可以清楚的看到程序的代码结构,其代码还存在混淆效果,提取的完整 PE 文件可直接运行,且其行为与原始样本相同;
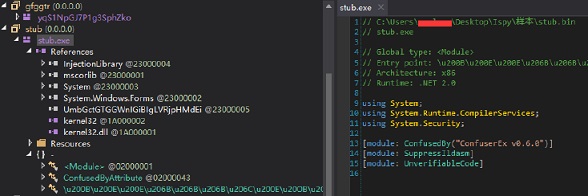
]2 解密后代码结构
提取加载资源 UmbGctGTGGWnIGiBIgLVRjpHMdEi.dll;查看提取的该模块信息,该程序的功能代码主要在该模块中定义,包括:反内存 dump,反沙箱,执行命令,下载文件,注入进程,自保护,监控屏幕,启动配置文件等信息;
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
0:000> !CLRStack
OS Thread Id: 0xadc (0)
ESP EIP
0032e7ac 6d9588b6 System.Convert.ChangeType(System.Object, System.Type, System.IFormatProvider)
0032e7c4 005d72a5 stub.exe!Unknown
0032e80c 005d60f9 stub.exe!Unknown*** WARNING: Unable to verify checksum for image01260000
*** ERROR: Module load completed but symbols could not be loaded for image01260000
0032eac4 6db31b4c [GCFrame: 0032eac4]
0032f068 6db31b4c [PrestubMethodFrame: 0032f068] stub.exe!Unknown
0032f28c 6db31b4c [GCFrame: 0032f28c]
0:000> !Name2EE *!UmbGctGTGGWnIGiBIgLVRjpHMdEi
Module: 6d031000 (mscorlib.dll)
———————————————————
Module: 00192360 (sortkey.nlp)
———————————————————
@NSFOCUS 2016 http://www.nsfocus.com
Module: 00192010 (sorttbls.nlp)
———————————————————
Module: 001926b0 (prcp.nlp)
———————————————————
Module: 00192a00 (mscorlib.resources.dll)
———————————————————
Module: 00172ff8 (stub.exe)
———————————————————
Module: 001745a4 (UmbGctGTGGWnIGiBIgLVRjpHMdEi, Version=0.0.0.0, Culture=neutral,
PublicKeyToken=null)
———————————————————
Module: 6c831000 (System.dll)
0:000> !DumpModule 001745a4
Name: UmbGctGTGGWnIGiBIgLVRjpHMdEi, Version=0.0.0.0, Culture=neutral, PublicKeyToken=null
Attributes: PEFile
Assembly: 00686338
LoaderHeap: 00000000
TypeDefToMethodTableMap: 0022405c
TypeRefToMethodTableMap: 00224064
MethodDefToDescMap: 00224068
FieldDefToDescMap: 0022406c
MemberRefToDescMap: 00224070
FileReferencesMap: 00224078
AssemblyReferencesMap: 0022407c
MetaData start address: 00443238 (284 bytes)
@NSFOCUS 2016 http://www.nsfocus.com
|
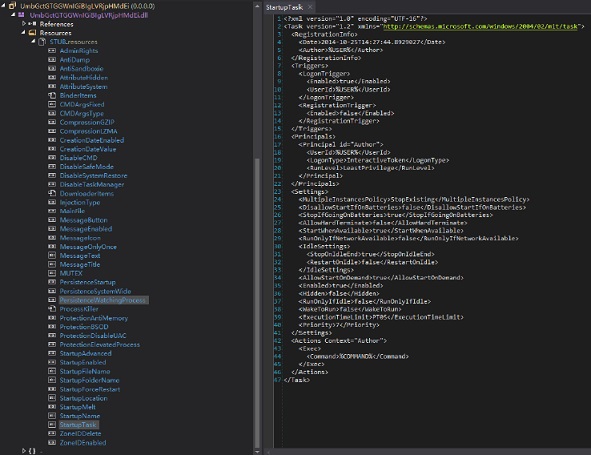
]3 功能模块
由于 stub.exe 被进行代码混淆处理,使用 windbg 直接调试 stub.exe 进行混淆代码反混淆处理,通过查看程序运行堆栈信息,可以确程序在是否进行代码还原完毕
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
ESP EIP
0036ea5c 77e6f8c1 [NDirectMethodFrameStandalone: 0036ea5c]
System.Net.UnsafeNclNativeMethods+OSSOCK.WSAConnect(IntPtr, Byte[], Int32, IntPtr, IntPtr, IntPtr,
IntPtr)
0036ea80 6c97228a System.Net.Sockets.Socket.DoConnect(System.Net.EndPoint,
System.Net.SocketAddress)*** WARNING: Unable to verify checksum for
C:\Windows\assembly\NativeImages_v2.0.50727_32\System\9e0a3b9b9f457233a335d7fba8f95419\Syst
em.ni.dll
0036eaa0 6c959144 System.Net.Sockets.Socket.InternalConnect(System.Net.EndPoint)
0036eab0 6c9515f1 System.Net.ServicePoint.ConnectSocketInternal(Boolean, System.Net.Sockets.Socket,
System.Net.Sockets.Socket, System.Net.Sockets.Socket ByRef, System.Net.IPAddress ByRef,
ConnectSocketState, System.IAsyncResult, Int32, System.Exception ByRef)
0036eb14 6c9514f9 System.Net.ServicePoint.ConnectSocket(System.Net.Sockets.Socket,
System.Net.Sockets.Socket, System.Net.Sockets.Socket ByRef, System.Net.IPAddress ByRef,
ConnectSocketState, Int32, System.Exception ByRef)
0036eb3c 6c95147c System.Net.ServicePoint.GetConnection(System.Net.PooledStream, System.Object,
Boolean, System.Net.IPAddress ByRef, System.Net.Sockets.Socket ByRef, System.Net.Sockets.Socket ByRef,
Int32)
0036eb7c 6c95135c System.Net.PooledStream.Activate(System.Object, Boolean, Int32,
@NSFOCUS 2016 http://www.nsfocus.com
System.Net.GeneralAsyncDelegate)
0036ebb8 6c95116a System.Net.Connection.CompleteStartConnection(Boolean,
System.Net.HttpWebRequest)
0036ec00 6c97978a System.Net.Connection.CompleteStartRequest(Boolean,
System.Net.HttpWebRequest, System.Net.TriState)
0036ec30 6c9790d3 System.Net.Connection.SubmitRequest(System.Net.HttpWebRequest)
0036ec74 6c978a2c System.Net.ServicePoint.SubmitRequest(System.Net.HttpWebRequest, System.String)
0036ecac 6c9782f9 System.Net.HttpWebRequest.SubmitRequest(System.Net.ServicePoint)
0036ecd8 6ce9de54 System.Net.HttpWebRequest.GetResponse()
0036ed18 6cce6db0 System.Net.WebClient.GetWebResponse(System.Net.WebRequest)
0036ed24 6cce87cb System.Net.WebClient.DownloadBits(System.Net.WebRequest, System.IO.Stream,
System.Net.CompletionDelegate, System.ComponentModel.AsyncOperation)
0036ed48 6cce6b53 System.Net.WebClient.DownloadDataInternal(System.Uri, System.Net.WebRequest
ByRef)
0036ed78 6cce7e43 System.Net.WebClient.DownloadString(System.Uri)
0036edac 6cce7dc6 System.Net.WebClient.DownloadString(System.String)
0036edb8 00622a19 Technitium.ComputerInformation.GetExternalIP()
0036ee04 00621b1b Technitium.ComputerInformation.GetInformation()
0036ef1c 00620ca6 Technitium.Core.FileExecuted()
0036f124 0062057c Technitium.Main.main()
0036f3c8 6db31b4c [GCFrame: 0036f3c8]
|
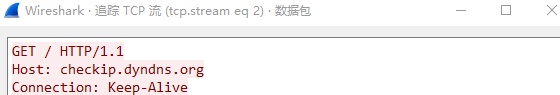
]4 获取外网 IP
通过上述脱壳反混淆处理后,提取该样本原始程序核心代码,进行代码分析,其代码中主要包含以下几个核心功能类:Technitium.Main、Technitium.Core、Technitium.RunPEx、Technitium.Config、Technitium.Stealer 等,下面是上述类的详细信息;
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
|
# Technitium.Config
1:006> !dumpmt –md 00183c64
EEClass: 00371b0c
Module: 00182ff8
Name: Technitium.Config
mdToken: 0200003a (C:\Users\bassx\Desktop\stub.exe)
BaseSize: 0xc
ComponentSize: 0x0
Number of IFaces in IFaceMap: 0
Slots in VTable: 7
———————————————————
MethodDesc Table
Entry MethodDesc JIT Name
6d1f6a90 6d07494c PreJIT System.Object.ToString()
@NSFOCUS 2016 http://www.nsfocus.com
6d1f6ab0 6d074954 PreJIT System.Object.Equals(System.Object)
6d1f6b20 6d074984 PreJIT System.Object.GetHashCode()
6d267540 6d0749a8 PreJIT System.Object.Finalize()
00620108 00183c48 JIT Technitium.Config..cctor()
0018c10d 00183c50 NONE Technitium.Config..ctor()
0018c111 00183c58 NONE Technitium.Config.DumpErrorLog(System.Exception, System.String)
# Technitium.Stealer
1:006> !dumpmt –md 00188760
EEClass: 003764e8
Module: 00182ff8
Name: Technitium.Stealer
mdToken: 02000022 (C:\Users\bassx\Desktop\stub.exe)
BaseSize: 0xc
ComponentSize: 0x0
Number of IFaces in IFaceMap: 0
Slots in VTable: 13
———————————————————
MethodDesc Table
Entry MethodDesc JIT Name
6d1f6a90 6d07494c PreJIT System.Object.ToString()
6d1f6ab0 6d074954 PreJIT System.Object.Equals(System.Object)
6d1f6b20 6d074984 PreJIT System.Object.GetHashCode()
6d267540 6d0749a8 PreJIT System.Object.Finalize()
0018c4b5 001886f8 NONE Technitium.Stealer..ctor()
00623918 00188700 JIT Technitium.Stealer.Recover()
0018c4bd 0018870c NONE Technitium.Stealer.MSParseLogs(System.String)
0018c4c1 00188718 NONE Technitium.Stealer.OSParseLogs(System.String)
0018c4c5 00188724 NONE Technitium.Stealer.MLParseLogs(System.String)
0018c4c9 00188730 NONE Technitium.Stealer.WBParseLogs(System.String)
0018c4cd 0018873c NONE Technitium.Stealer.WaitUntilFileIsAvailable(System.String)
00624080 00188748 JIT Technitium.Stealer.Decompress(Byte[])
00623fd0 00188754 JIT Technitium.Stealer.Cloud(System.String)
# Technitium.RunPEx
1:006> !dumpmt –md 00188c2c
EEClass: 0037688c
Module: 00182ff8
Name: Technitium.RunPEx
mdToken: 02000040 (C:\Users\bassx\Desktop\stub.exe)
BaseSize: 0xc
ComponentSize: 0x0
Number of IFaces in IFaceMap: 0
Slots in VTable: 15
———————————————————
MethodDesc Table
@NSFOCUS 2016 http://www.nsfocus.com
Entry MethodDesc JIT Name
6d1f6a90 6d07494c PreJIT System.Object.ToString()
6d1f6ab0 6d074954 PreJIT System.Object.Equals(System.Object)
6d1f6b20 6d074984 PreJIT System.Object.GetHashCode()
6d267540 6d0749a8 PreJIT System.Object.Finalize()
0018c60d 00188aac NONE Technitium.RunPEx..ctor()
0018c64c 00188ab4 NONE Technitium.RunPEx.CreateProcess(System.String, System.String,
IntPtr, IntPtr, Boolean, UInt32, IntPtr, System.String, STARTUP_INFORMATION ByRef,
PROCESS_INFORMATION ByRef)
0018c658 00188ad8 NONE Technitium.RunPEx.GetThreadContext(IntPtr, Int32[])
0018c694 00188afc NONE Technitium.RunPEx.SetThreadContext(IntPtr, Int32[])
0018c664 00188b20 NONE Technitium.RunPEx.ReadProcessMemory(IntPtr, Int32, Int32 ByRef,
Int32, Int32 ByRef)
0018c688 00188b44 NONE Technitium.RunPEx.WriteProcessMemory(IntPtr, Int32, Byte[], Int32,
Int32 ByRef)
0018c670 00188b68 NONE Technitium.RunPEx.NtUnmapViewOfSection(IntPtr, Int32)
0018c67c 00188b8c NONE Technitium.RunPEx.VirtualAllocEx(IntPtr, Int32, Int32, Int32, Int32)
0018c6a0 00188bb0 NONE Technitium.RunPEx.ResumeThread(IntPtr)
006241d0 00188bd4 JIT Technitium.RunPEx.Run(System.String, System.String, Byte[], Boolean,
Boolean)
00624270 00188be0 JIT Technitium.RunPEx.HandleRun(System.String, System.String, Byte[],
Boolean, Boolean)
# Technitium.Main
1:006> !dumpmt –md 001838dc
EEClass: 003715cc
Module: 00182ff8
Name: Technitium.Main
mdToken: 02000002 (C:\Users\bassx\Desktop\stub.exe)
BaseSize: 0xc
ComponentSize: 0x0
Number of IFaces in IFaceMap: 0
Slots in VTable: 25
———————————————————
MethodDesc Table
Entry MethodDesc JIT Name
6d1f6a90 6d07494c PreJIT System.Object.ToString()
6d1f6ab0 6d074954 PreJIT System.Object.Equals(System.Object)
6d1f6b20 6d074984 PreJIT System.Object.GetHashCode()
6d267540 6d0749a8 PreJIT System.Object.Finalize()
00620070 001836e4 JIT Technitium.Main..cctor()
00620440 001836ec JIT Technitium.Main.main()
0018c079 001836f8 NONE Technitium.Main.ProProtect()
0018c07d 00183704 NONE Technitium.Main.Disablers()
0018c081 00183710 NONE Technitium.Main.AV()
@NSFOCUS 2016 http://www.nsfocus.com
0018c085 0018371c NONE Technitium.Main.Bot()
0018c089 00183728 NONE Technitium.Main.ProcessP()
0018c08d 00183734 NONE Technitium.Main.SendLogs()
0018c091 00183740 NONE Technitium.Main.UnhookWindowsHookEx(Int32)
0018c095 00183764 NONE Technitium.Main.SetWindowsHookEx(Int32, KeyboardHookDelegate,
Int32, Int32)
0018c099 00183788 NONE Technitium.Main.GetAsyncKeyState(Int32)
0018c09d 001837ac NONE Technitium.Main.CallNextHookEx(Int32, Int32, Int32,
KBDLLHOOKSTRUCT)
0018c0a1 001837d0 NONE Technitium.Main.lineSetAppSpecific(Int64, Int64)
0018c0a5 001837f4 NONE Technitium.Main.MgmGetNextMfeStats(IntPtr ByRef, Int64 ByRef,
System.String ByRef, Int64 ByRef)
0018c0a9 00183818 NONE Technitium.Main.GetForegroundWindow()
0018c0ad 0018383c NONE Technitium.Main.GetWindowText(Int32, System.String ByRef, Int32)
0018c0b1 00183860 NONE Technitium.Main.GetActiveWindowTitle()
0018c0b5 0018386c NONE Technitium.Main.Hooked()
0018c0b9 00183878 NONE Technitium.Main.HookKeyboard()
0018c0bd 00183884 NONE Technitium.Main.UnhookKeyboard()
0018c0c1 00183890 NONE Technitium.Main.KeyboardCallback(Int32, Int32, KBDLLHOOKSTRUCT
ByRef)
# Technitium.Core
1:006> !dumpmt –md 001849e0
EEClass: 00371d0c
Module: 00182ff8
Name: Technitium.Core
mdToken: 0200003b (C:\Users\bassx\Desktop\stub.exe)
BaseSize: 0xc
ComponentSize: 0x0
Number of IFaces in IFaceMap: 0
Slots in VTable: 23
———————————————————
MethodDesc Table
Entry MethodDesc JIT Name
6d1f6a90 6d07494c PreJIT System.Object.ToString()
6d1f6ab0 6d074954 PreJIT System.Object.Equals(System.Object)
6d1f6b20 6d074984 PreJIT System.Object.GetHashCode()
6d267540 6d0749a8 PreJIT System.Object.Finalize()
0018c141 001848b0 NONE Technitium.Core..ctor()
0018c145 001848b8 NONE Technitium.Core.CreateAPI(System.String, System.String)
0018c149 001848cc NONE Technitium.Core.CallAPI(System.String, System.String, System.Type[],
System.Object[])
0018c14d 001848e0 NONE Technitium.Core.GetInstallPath()
0018c151 001848ec NONE Technitium.Core.IsAdmin()
0018c155 001848f8 NONE Technitium.Core.RecoverPasswords()
@NSFOCUS 2016 http://www.nsfocus.com
00620740 00184904 JIT Technitium.Core.Decrypt()
0018c15d 00184910 NONE Technitium.Core.DeleteSavedPasswords()
0018c161 0018491c NONE Technitium.Core.UploadScreenshot()
0018c165 00184928 NONE Technitium.Core.GenerateHWID()
0018c169 00184934 NONE Technitium.Core.MD5(System.String)
0018c16d 00184940 NONE Technitium.Core.GetVolumeInformationA(System.String ByRef,
System.String ByRef, UInt32, UInt32 ByRef, UInt32 ByRef, UInt32 ByRef, System.String ByRef, UInt32)
0018c171 00184964 NONE Technitium.Core.HidD_GetHidGuid(System.Guid ByRef)
00620bd8 00184988 JIT Technitium.Core.FileExecuted()
0018c179 00184994 NONE Technitium.Core.Install()
0018c17d 001849a0 NONE Technitium.Core.IsConnectedToInternet()
0018c181 001849ac NONE Technitium.Core.Startup(System.Object)
0018c185 001849b8 NONE Technitium.Core.FakeMessage()
0018c189 001849c4 NONE Technitium.Core.Upload(System.String, System.String, System.String)
|
0x01 功能分析
iSpySoft 木马实现了多种功能,包括:窃取用户信息、浏览器信息(登录用户名密码)、键盘监控、截屏、视频监控、文件下载、文件上传、远程控制等功能。
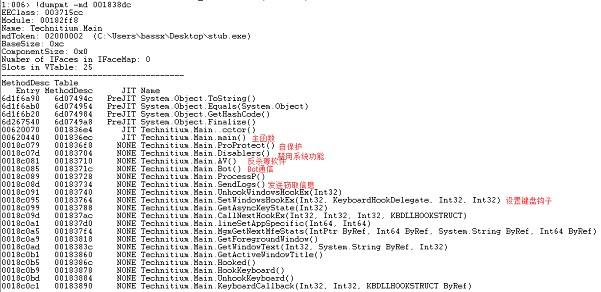
]5 主模块功能
下面是对其主功能函数的分析, 主函数执行的功能主要依赖于其配置信息, 通过对其配置选项执行相应的功能函数;
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
|
# Technitium.Main.main() 主功能函数
1:006> !dumpil 001836ec
ilAddr = 004020a4
IL_0000: nop
.try
{
IL_0001: nop
IL_0002: ldsfld Technitium.Config::DELAY_EXECUTION # 读取配置参数
IL_0007: call System.Convert::ToInt32
IL_000c: ldc.i4 1000
IL_0011: mul.ovf
IL_0012: call System.Threading.Thread::Sleep
@NSFOCUS 2016 http://www.nsfocus.com
IL_0017: nop
IL_0018: ldsfld Technitium.Config::ANTI_DEBUGGERS # 读取配置参数
IL_001d: call System.String::IsNullOrEmpty
IL_0022: ldc.i4.0
IL_0023: ceq
IL_0025: stloc.1
IL_0026: ldloc.1
IL_0027: brfalse.s IL_0030
IL_0029: newobj AntiDebugger::.ctor
IL_002e: stloc.2
IL_002f: nop
IL_0030: nop
IL_0031: ldc.i4.0
IL_0032: stloc.0
IL_0033: nop
IL_0034: ldc.i4.1
IL_0035: ldsfld Technitium.Config::MUTEX
IL_003a: ldloca.s VAR OR ARG 0
IL_003c: newobj System.Threading.Mutex::.ctor
IL_0041: stloc.3
.try
{
IL_0042: ldloc.0
IL_0043: stloc.s VAR OR ARG 4
IL_0045: ldloc.s VAR OR ARG 4
IL_0047: brfalse IL_010e
IL_004c: call Technitium.Core::Decrypt
IL_0051: nop
IL_0052: ldsfld Technitium.Config::INSTALL_FILE # 读取配置参数
IL_0057: call System.String::IsNullOrEmpty
IL_005c: ldc.i4.0
IL_005d: ceq
IL_005f: stloc.s VAR OR ARG 5
IL_0061: ldloc.s VAR OR ARG 5
IL_0063: brfalse.s IL_006c
IL_0065: call Technitium.Core::Install
IL_006a: nop
IL_006b: nop
IL_006c: nop
IL_006d: call Technitium.Core::FileExecuted
IL_0072: nop
IL_0073: ldsfld Technitium.Config::KEYSTROKES # 读取配置参数
IL_0078: call System.String::IsNullOrEmpty
IL_007d: ldc.i4.0
@NSFOCUS 2016 http://www.nsfocus.com
IL_007e: ceq
IL_0080: stloc.s VAR OR ARG 6
IL_0082: ldloc.s VAR OR ARG 6
IL_0084: brfalse.s IL_00cb
IL_0086: ldstr “..[— Window: “
IL_008b: stsfld Technitium.Main::LHeader
IL_0090: ldstr ” —]..”
IL_0095: stsfld Technitium.Main::RHeader
IL_009a: call Technitium.Main::HookKeyboard
IL_009f: nop
IL_00a0: ldc.i4.1
IL_00a1: stsfld Technitium.Main::UseCaps
IL_00a6: ldnull
IL_00a7: ldftn Technitium.Main::SendLogs
IL_00ad: newobj System.Threading.ThreadStart::.ctor
IL_00b2: newobj System.Threading.Thread::.ctor
IL_00b7: stloc.s VAR OR ARG 7
IL_00b9: ldloc.s VAR OR ARG 7
IL_00bb: ldc.i4.0
IL_00bc: callvirt System.Threading.Thread::SetApartmentState
IL_00c1: nop
IL_00c2: ldloc.s VAR OR ARG 7
IL_00c4: callvirt System.Threading.Thread::Start
IL_00c9: nop
IL_00ca: nop
IL_00cb: nop
IL_00cc: call Technitium.Main::Disablers
IL_00d1: nop
IL_00d2: call Technitium.Main::AV
IL_00d7: nop
IL_00d8: call Technitium.Main::Bot
IL_00dd: nop
IL_00de: call Technitium.Main::ProProtect
IL_00e3: nop
IL_00e4: ldsfld Technitium.Config::RUNESCAPE_PINLOGGER # 读取配置参数
IL_00e9: call System.String::IsNullOrEmpty
IL_00ee: ldc.i4.0
IL_00ef: ceq
IL_00f1: stloc.s VAR OR ARG 8
IL_00f3: ldloc.s VAR OR ARG 8
IL_00f5: brfalse.s IL_010a
IL_00f7: ldnull
IL_00f8: ldftn Technitium.Pinlogger::Log
IL_00fe: newobj System.Threading.WaitCallback::.ctor
@NSFOCUS 2016 http://www.nsfocus.com
IL_0103: call System.Threading.ThreadPool::QueueUserWorkItem
IL_0108: pop
IL_0109: nop
IL_010a: nop
IL_010b: nop
IL_010c: br.s IL_0117
IL_010e: nop
IL_010f: ldc.i4.0
IL_0110: call System.Environment::Exit
IL_0115: nop
IL_0116: nop
IL_0117: leave.s IL_0125
} // end .try
.finally
{
IL_0119: nop
IL_011a: ldloc.3
IL_011b: brfalse.s IL_0124
IL_011d: ldloc.3
IL_011e: callvirt System.IDisposable::Dispose
IL_0123: nop
IL_0124: endfinally
} // end .finally
IL_0125: call System.Diagnostics.Process::GetCurrentProcess
IL_012a: callvirt System.Diagnostics.Process::WaitForExit
IL_012f: nop
IL_0130: leave.s IL_0151
} // end .try
.catch
{
IL_0132: dup
IL_0133: call Microsoft.VisualBasic.CompilerServices.ProjectDat::SetProjectError
IL_0138: stloc.s VAR OR ARG 9
IL_013a: nop
IL_013b: ldloc.s VAR OR ARG 9
IL_013d: callvirt System.Exception::ToString
IL_0142: ldc.i4.0
IL_0143: ldnull
IL_0144: call Microsoft.VisualBasic.Interaction::MsgBox
IL_0149: pop
IL_014a: call Microsoft.VisualBasic.CompilerServices.ProjectDat::ClearProjectError
IL_014f: leave.s IL_0151
} // end .catch
IL_0151: nop
@NSFOCUS 2016 http://www.nsfocus.com
IL_0152: ret
|
iSpySoft 木马主要配置文件
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
|
# Technitium.Config..cctor() 配置文件
1:006> !dumpil 00183c48
ilAddr = 00407b3c
IL_0000: ldstr “1.0.0.0”
IL_0005: stsfld Technitium.Config::VERSION # 版本
IL_000a: ldstr “AF7B1841C6A70C858E3201422E2D0BEA”
IL_000f: stsfld Technitium.Config::HWID # HWID
IL_0014: ldstr “149ff47a-7df2-4b42-823e-2820d63034b4”
IL_0019: stsfld Technitium.Config::MUTEX # iSpy MUTEX
IL_001e: ldstr “EMAIL”
IL_0023: stsfld Technitium.Config::UPLOAD_METHOD # 上传文件方式, 提供三种 EMAIL, FTP,
IL_0028: ldstr “XXXXXXXXXXXXXXX”
IL_002d: stsfld Technitium.Config::EMAIL_USERNAME # EMAIL 用户名
IL_0032: ldstr “XXXXXXXXXXXXXXX”
IL_0037: stsfld Technitium.Config::EMAIL_PASSWORD # EMAIL 密码
IL_003c: ldstr “XXXXXXXXXXXXXXX”
IL_0041: stsfld Technitium.Config::EMAIL_PORT # EMAIL 端口
IL_0046: ldstr “XXXXXXXXXXXXXXX”
IL_004b: stsfld Technitium.Config::EMAIL_SERVER # EMAIL 服务器
IL_0050: ldstr “”
IL_0055: stsfld Technitium.Config::EMAIL_SSL # 是否开发 SSL
IL_005a: ldstr “XXXXXXXXXXXXXXX”
IL_005f: stsfld Technitium.Config::FTP_USERNAME # Ftp 用户名
IL_0064: ldstr “XXXXXXXXXXXXXXX”
IL_0069: stsfld Technitium.Config::FTP_PASSWORD # Ftp 密码
IL_006e: ldstr “XXXXXXXXXXXXXXX”
IL_0073: stsfld Technitium.Config::FTP_SERVER # Ftp 服务器
IL_0078: ldstr “XXXXXXXXXXXXXXX”
IL_0082: ldstr “XXXXXXXXXXXXXXX”
IL_008c: ldstr “10”
IL_0091: stsfld Technitium.Config::LOG_INTERVAL
IL_0096: ldstr “”
IL_009b: stsfld Technitium.Config::CLIPBOARD_MONITORING # 监控剪切板
IL_00a0: ldstr “”
IL_00a5: stsfld Technitium.Config::SEND_SCREENSHOTS # 发送截屏信息
IL_00aa: ldstr “”
IL_00af: stsfld Technitium.Config::KEYSTROKES # 进行按键监控
IL_00b4: ldstr “”
@NSFOCUS 2016 http://www.nsfocus.com
IL_00b9: stsfld Technitium.Config::WEBCAM_LOGGER # 摄像头监控
IL_00be: ldstr “”
IL_00c3: stsfld Technitium.Config::MODIFY_TASK_MANAGER # 禁用任务管理器
IL_00c8: ldstr “”
IL_00cd: stsfld Technitium.Config::ANTI_DEBUGGERS # 检测调试器
IL_00d2: ldstr “”
IL_00d7: stsfld Technitium.Config::PROCESS_PROTECTION # 程序自保护
IL_00dc: ldstr “”
IL_00e1: stsfld Technitium.Config::RUNESCAPE_PINLOGGER
IL_00e6: ldstr “”
IL_00eb: stsfld Technitium.Config::CLEAR_SAVED
IL_00f0: ldstr “2a76d583-f7dc-4bb6-88eb-6515438f2ee7”
IL_00f5: stsfld Technitium.Config::PASSWORD_STEALER # 窃取密码
IL_00fa: ldstr “”
IL_00ff: stsfld Technitium.Config::MELT_FILE
IL_0104: ldstr “”
IL_0109: stsfld Technitium.Config::INSTALL_FILE # 安装文件
IL_010e: ldstr “[PATHTYPE]”
IL_0113: stsfld Technitium.Config::PATH_TYPE # 安装路径
IL_0118: ldstr “[FOLDER]”
IL_011d: stsfld Technitium.Config::FOLDER_NAME # 安装文件夹名称
IL_0122: ldstr “[FILENAME]”
IL_0127: stsfld Technitium.Config::FILE_NAME # 安装文件名称
IL_012c: ldstr “”
IL_0131: stsfld Technitium.Config::HKCU # 注册表配置 1
IL_0136: ldstr “”
IL_013b: stsfld Technitium.Config::HKLM # 注册表配置 2
IL_0140: ldstr “”
IL_0145: stsfld Technitium.Config::BINDER # 绑定端口
IL_014a: ldstr “”
IL_014f: stsfld Technitium.Config::VISIT_WEBSITE # 访问网站
IL_0154: ldstr “”
IL_0159: stsfld Technitium.Config::BLOCKER_WEBSITE # 阻断网站
IL_015e: ldstr “”
IL_0163: stsfld Technitium.Config::REGISTRY_PERSISTENCE
IL_0168: ldstr “”
IL_016d: stsfld Technitium.Config::HIDE_FILE # 隐藏文件
IL_0172: ldstr “”
IL_0177: stsfld Technitium.Config::DOWNLOAD_FILE # 下载文件
IL_017c: ldstr “”
IL_0181: stsfld Technitium.Config::DOWNLOAD_FILE_TYPE # 下载文件类型
IL_0186: ldstr “”
IL_018b: stsfld Technitium.Config::MESSAGE_TYPE # 消息类型定义
IL_0190: ldstr “[MTITLE]”
@NSFOCUS 2016 http://www.nsfocus.com
IL_0195: stsfld Technitium.Config::MESSAGE_TITLE # 消息头定义
IL_019a: ldstr “[MBODY]”
IL_019f: stsfld Technitium.Config::MESSAGE_BODY # 消息内容定义
IL_01a4: ldstr “”
IL_01a9: stsfld Technitium.Config::DISABLERS # 禁用系统功能 cmd
IL_01ae: ldstr “”
IL_01b3: stsfld Technitium.Config::BOT_KILLER # 关闭 Bot 功能
IL_01b8: ldstr “”
IL_01bd: stsfld Technitium.Config::ANTIVIRUS_KILLER # 关闭杀毒软件
IL_01c2: ldstr “0”
IL_01c7: stsfld Technitium.Config::DELAY_EXECUTION # 延迟执行
IL_01cc: ret
|
]6 窃取密码
通过对该木马中的配置文件分析,其主要功能是实现密码窃取(其他功能项未配置),并且配置实用 EMAIL 方式上传收集到的用户密码信息。
0x02 窃取密码
通过邮件方式窃取收集到的用户密码信息:
]7 Wireshark 抓包
从获取的网络数据包看出内容是经过 base64 编码的,将其解码后内容如下:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
Dear iSpy Keylogger Customers,
Let us informed you that iSpy Keylogger is currently active now.
Best Regards
iSpySoft Admin
*********** Computer Information ***********
Username: WIN–86JN3PJSB51
Windows Installed: Microsoft Windows 7 家庭普通版
Local Date & Time: 2016/4/22 16:13:13
Installed Language: zh–CN
.NET Framework Installed: 2, 4
System Privileges: User
Default Browser: Not found!
Installed Anti–Virus:
Installed Firewall:
Internal IP: 192.168.78.130
External IP:
*********** Computer Information ***********
|
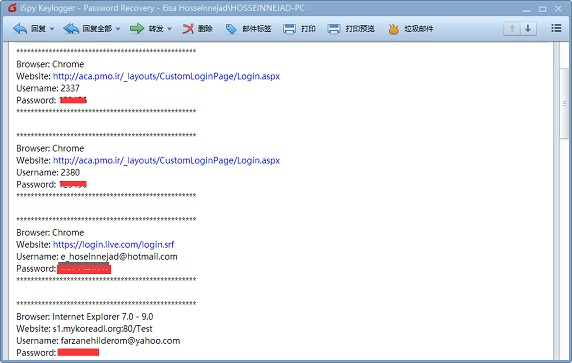
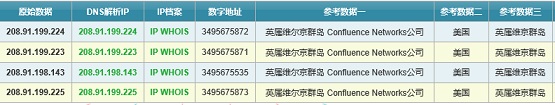
通过配置文件中的 EMAIL 配置信息,登录攻击者邮箱,其中,存在其已经获取到的用户信息:
]8 攻击者邮箱
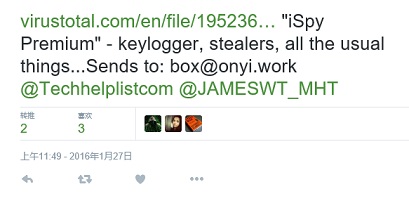
0x03 样本跟踪
iSpySoft木马最早被出现于2016年1月27日,发展至今,其木马功能强大,最新版的程序使用 ConfuserEx v0.6.0 加密混淆器对其代码进行了处理。
0x04 行为分析
0x05 攻击目标定位
0x06 系统检测
0x07 绿盟科技专杀解决方案
短期服务:绿盟科技工程师现场木马后门清理服务(人工服务+IPS+TAC)。确保第一时间消除网络内相关风险点,控制事件影响范围,提供事件分析报告。 中期服务:提供 3-6 个月的风险监控与巡检服务(IPS+TAC+人工服务)。根除风险,确保事件不复发。 长期服务:基金行业业务风险解决方案(威胁情报+攻击溯源+专业安全服务)。
如果您需要了解更多内容,可以
加入QQ群:486207500