摘要: 注:早上有朋友和我说,另外有账号发布的排名不是这样——游侠专门去看了下,然后又去美国人的网站看了下,确认游侠安全网同步的这个排名是目前最新,且没有任何错误的版本! 美国第三方调研机构的“网络安全创新500强”榜单更新,在此次榜单中,依然和此前一样,有4家中国安...
注:早上有朋友和我说,另外有账号发布的排名不是这样——游侠专门去看了下,然后又去美国人的网站看了下,确认游侠安全网同步的这个排名是目前最新,且没有任何错误的版本!
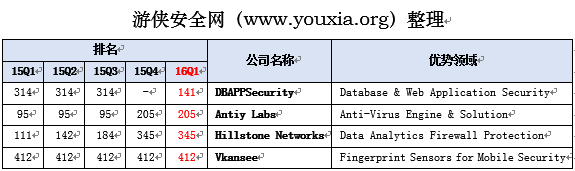
美国第三方调研机构的“网络安全创新500强”榜单更新,在此次榜单中,依然和此前一样,有4家中国安全公司上榜。他们是:
- DBAPPSecurity(安恒信息)
- Antiy Labs(安天实验室)
- Hillstone Networks(山石网科)
- Vkansee
游侠安全网特意整理了下2015年Q1-Q4以及2016年Q1的排名,这样大家可以非常容易的对比这个排名:
DBAppSecurity:在最新的榜单中,安恒信息是排名最高的中国网络安全公司,从此前一直是314,2015Q4甚至排在了500名开外,但2016Q1一跃到了141——这可能和安恒最近发布的产品有关:2月29日(明天),安恒即将在RSA大会上公布新产品——云安全监测服务及平台(风暴中心)、APT Discovery Platform(APT攻击预警平台) , Cloud WAF(云WAF,玄武盾), Cloud-based LogAudit (云日志审计,飞天镜),Cloud-based USMB(云堡垒机),这算不算是提前1天的“剧透”?由于产品集中在云安全、APT、大数据领域,所以排名大幅上升是非常容易理解的。
RSA 2016安恒展台:S2435
Antiy Labs:相对于2015年前三个季度,安天2015Q4、2016Q1的排名发生了后退现象。可能很多人不太熟悉安天,但是作为传统反病毒领域的“技术控”,安天在病毒检测领域一直做的有声有色——特别是在国外市场。安天2016年重点集中在移动安全领域,大家可以持续关注!另外补充下:国内很多安全公司的病毒检测引擎,以及不少知名品牌的移动安全产品,都是用的安天引擎,只不过由于商务因素没有公布而已。个人认为如果安天如果把一些合作伙伴名单发布、再公布个新产品的话,排名会上升。
RSA 2016安天展台:S744
Hillstone Networks:山石网科的排名居然也靠后了……如果说传统防火墙、下一代防火墙、智能防火墙领域的排名的话,这不意外,但是山石网科最近的新产品:云界、云格还是蛮有竞争力——特别是后者,是非常有特色,以及有非常强的竞争力!(简单说就是实现云环境下虚拟机的数据隔离和安全防护),至少在中国范围内做的极少,有实力的更少,全球范围内能做到这样细粒度的也不多。
RSA 2016山石展台:展台S1639
Vkansee:从2015年Q1开始,到2016年Q1,Vkansee依然雷打不动的保持412的排名,游侠不知道为什么……在搜索引擎搜了下这个公司,说的总部在中国北京,在美国有办事机构,但是官方网站没有中文。所以游侠也就不知道他们的中文名称是什么。但有一句话特别引人注意,就是他们的投资方包括:AVIC——中国航空工业集团。
2015年2季度的一些信息游侠安全网亦有报道,可以点 这里 查看。这里 查看。
因为官方网站打开速度较慢,所以游侠把这TOP 500的名单复制了一份过来,各位看看:
| # | Company | Cybersecurity Sector |
| 1 | root9B | Adversary Pursuit & Cyber Operations |
| 2 | RSA | Intelligence Driven Security |
| 3 | IBM Security | Enterprise IT Security Solutions |
| 4 | Dell SecureWorks | Managed Security Services |
| 5 | Palo Alto Networks | Threat Detection & Prevention |
| 6 | Cisco | Threat Protection & Network Security |
| 7 | Fortinet | Mobile, IoT & Cloud Security |
| 8 | BT | Security & Risk Management Solutions |
| 9 | FireEye | Advanced Threat Protection |
| 10 | Herjavec Group | Information Security Services |
| 11 | Clearwater Compliance | Risk Management and Compliance |
| 12 | Symantec | Endpoint, Cloud & Mobile Security |
| 13 | Trend Micro | Server, Cloud, and Content Security |
| 14 | Forcepoint | Cloud, Mobility & IoT Security |
| 15 | CyberArk | Cyber Threat Protection |
| 16 | Sera-Brynn | Cyber Risk Management |
| 17 | Sophos | Anti-Virus & Malware Protection |
| 18 | Intel Security Group | Anti-Virus, Malware & Threat Protection |
| 19 | IKANOW | Information Security Analytics |
| 20 | Cavirin | IT Infrastructure Security |
| 21 | Digital Defense | Managed Security Risk Assessment |
| 22 | Rapid7 | Security Data & Analytics Solution |
| 23 | Veracode | Application Security Testing |
| 24 | Nexusguard | Cloud Enabled DDoS Mitigation |
| 25 | Thycotic | Privileged Account Management |
| 26 | Check Point Software | Unified Threat Management |
| 27 | Deloitte | Global Risk Management Services |
| 28 | Kaspersky Lab | Malware & Anti-Virus Solutions |
| 29 | Splunk | Big Data Security |
| 30 | DFLabs | Automated Incident & Breach Response |
| 31 | Code Dx | Software Assurance Analytics |
| 32 | Tenable Network Security | Vulnerability Scanning |
| 33 | Ziften | Endpoint Threat Detection |
| 34 | A10 Networks | DDoS Cyber Attack Protection |
| 35 | Booz Allen | Cybersecurity Solutions & Services |
| 36 | PwC | Cybersecurity Consulting & Advisory |
| 37 | Immuniweb | Continuous & On-Demand Web Security |
| 38 | Black Duck Software | Open Source Software Security |
| 39 | Bit9 + Carbon Black | Endpoint & Server Security Platform |
| 40 | Pindrop Security | Phone-Based Fraud Prevention |
| 41 | Proofpoint | Security-as-a-Service |
| 42 | EY | Cybersecurity Advisory Services |
| 43 | Bayshore Networks | Internet of Things Security |
| 44 | Imperva | Data & Applications Security |
| 45 | CYBERBIT | Cyber Security & Intelligence Solutions |
| 46 | FinalCode | File Encryption & IRM Platform |
| 47 | DB Networks | Intelligent Continuous Monitoring |
| 48 | Cryptzone | File & Data Encryption Platform |
| 49 | Cybera | Security Infrastructure Protection |
| 50 | i-Sprint | Identity & Access Management |
| 51 | Silent Circle | Enterprise Privacy Platform |
| 52 | Deep Secure | Content Control & Inspection |
| 53 | Checkmarx | Software Development Security |
| 54 | Northrop Grumman | Cyber & Homeland Security Services |
| 55 | L-3 | National Security Solutions |
| 56 | Tanium | Security & Systems Management |
| 57 | Qualys | Cloud Security & Compliance |
| 58 | AlienVault | Threat Detection & Response |
| 59 | SentryBay | PC, Mobile & IoT Security |
| 60 | Corero | DDoS Defense & Security Solutions |
| 61 | VMware | Mobile, Data Center & Cloud Security |
| 62 | HP | Cybersecurity for Public Sector & Defense |
| 63 | Palantir | Cybersecurity Analytics and Cyber Fraud |
| 64 | Threat Stack | Cloud Security Monitoring |
| 65 | Lockheed Martin | Cybersecurity Solutions & Services |
| 66 | Stroz Friedberg | Cyber Intelligence & Risk Management |
| 67 | Verizon Enterprise | Network & Data Security |
| 68 | Akamai Technologies | Secure Cloud & Mobile Computing |
| 69 | Tripwire | Advanced Cyberthreat Detection |
| 70 | Morphick | Advanced Threat Protection Services |
| 71 | StratoKey | Cloud Data Protection |
| 72 | AVG Technologies | Anti-Virus & Internet Security Software |
| 73 | TraceSecurity | IT Governance, Risk & Compliance |
| 74 | Coalfire | Cyber Risk Management |
| 75 | Cimcor | Governance, Risk & Compliance |
| 76 | Lookingglass | Cyber Threat Intelligence Management |
| 77 | Illumio | Adaptive Security Platform |
| 78 | Clearswift | Data Loss Prevention |
| 79 | Novetta | Cyber Security Analytics |
| 80 | Courion | Identity & Access Management |
| 81 | Leidos | Anti-Terrorism & Homeland Security |
| 82 | Level 3 | Network & Managed Security Services |
| 83 | MobileIron | Mobile Device & App Security |
| 84 | Click Security | Real Time Security Analytics |
| 85 | Autonomic Software | Patch & Endpoint Management |
| 86 | Accenture | Enterprise Security Strategy |
| 87 | PKWARE | Data Encryption & Security |
| 88 | StrikeForce Technologies | Keystroke Encryption & Mobile Security |
| 89 | ESNC | Security for SAP Applications |
| 90 | SnoopWall | Mobile Device Security |
| 91 | Optiv | Information Security Services |
| 92 | Bay Dynamics | Informaton Risk Intelligence |
| 93 | Blue Coat | Business Assurance Technology |
| 94 | Arbor Networks | DDoS Attack & Threat Proection |
| 95 | Future Tense Central | Phone & Mobile Device Security |
| 96 | Malwarebytes | Malware Detection & Protection |
| 97 | Fireglass | Enterprise Network Security |
| 98 | NetIQ | Security Management & Intelligence |
| 99 | Digital Guardian | Data Loss Prevention |
| 100 | Seculert | Cloud-Based Malware Protection |
| 101 | LIFARS | Digital Forensics & Cybersecurity Intelligence |
| 102 | Bwise | IT Governance, Risk & Compliance |
| 103 | Spam Titan | Email Security Appliances |
| 104 | AhnLab | Internet Security Solutions |
| 105 | Gemalto | Digital Identity Management |
| 106 | CloudLock | Cloud Information Security |
| 107 | Axway | Secure Email & File Sharing |
| 108 | Zscaler | Security-as-a-Service Solutions |
| 109 | Xceedium | Privileged Identity Management |
| 110 | Fidelis Cybersecurity | Cyber Attack Defense |
| 111 | Brinqa | Risk Analytics & Management |
| 112 | SurfRight | Malware Detection & Protection |
| 113 | Alert Logic | Security-as-a-Service Solutions |
| 114 | Avira | Antivirus & IT Security Software |
| 115 | DigiCert | Digital Certificate Provider |
| 116 | Spikes Security | Browser Malware Isolation |
| 117 | Elastica | Cloud Application Security |
| 118 | RiskVision | Integrated Risk Management |
| 119 | itWatch | Endpoint Security & Data Loss Prevention |
| 120 | Webroot | Security Analysis & Threat Detection |
| 121 | Arxan | Application Security Products |
| 122 | Entrust | Authentication & Identity Assurance |
| 123 | CenterTools Software | Endpoint Security Solutions |
| 124 | NowSecure | Mobile Device & App Security |
| 125 | Resilient Systems | Incident Response Platform |
| 126 | Confer | Threat Prevention & Incident Response |
| 127 | CYREN | Web, Email & Mobile Security |
| 128 | Tapestry Technologies | Cyber Defense Services |
| 129 | Enforcive | Data Security Software |
| 130 | Vaultive | Cloud Data Encryption |
| 131 | VASCO Data Security | Authentication & e-Signature Solutions |
| 132 | Silobreaker | Cyber Analytics & Risk Intelligence |
| 133 | ZixCorp | Email Encryption & Data Protection |
| 134 | Bitdefender | Anti-Virus & Endpoint Security |
| 135 | neXus | PKI, Access & Identity Management |
| 136 | Thales | Secure IT Solutions |
| 137 | cryptovision | Cryptography & Electronic Identity |
| 138 | ZeroFOX | Social Risk Management |
| 139 | CyFIR | Digital Forensics & e-Discovery |
| 140 | Bromium | Endpoint Security |
| 141 | DBAPPSecurity | Database & Web Application Security |
| 142 | CA Technologies | Enterprise IT Security |
| 143 | DomainTools | Cybercrime Investigation & Prevention |
| 144 | WWPass | Authentication & Access Solutions |
| 145 | Wombat Security Technologies | Cybersecurity Education & Training |
| 146 | ePlus Security | Infosecurity Services & Products |
| 147 | Globalscape | Secure File Transfer |
| 148 | AT&T Network Security | Managed Security & Consulting |
| 149 | wolfSSL | Open Source Internet Security |
| 150 | Varonis | File Collaboration & Data Protection |
| 151 | Haystax | Advanced Threat Analytics |
| 152 | Voltage Security | Data Encryption & Key Management |
| 153 | Venafi | Trust Protection Platform |
| 154 | Viewfinity | Threat Detection & Protection |
| 155 | Vormetric | Data Security Solutions |
| 156 | Unisys | Endpoint & IT Infrastructure Security |
| 157 | Trustwave | Managed Security Services |
| 158 | TechGuard | National Cyber Defense |
| 159 | Bradford Networks | Network Security Automation |
| 160 | Rsam | IT Governance, Risk & Compliance |
| 161 | CloudLink | Cloud Security & Data Encryption |
| 162 | Skyhigh Networks | Cloud Access Security |
| 163 | SynerComm | Network & Security Infrastructure |
| 164 | AccelOps | Network Security Monitoring |
| 165 | ThreatMetrix | Online & Mobile Fraud Protection |
| 166 | TrustedSec | Information Security Consulting |
| 167 | Shape Security | Website Attack Prevention |
| 168 | SAIC | Cybersecurity Professional Services |
| 169 | V-Key | Mobile App Security |
| 170 | Centrify | Unified Identity Management |
| 171 | Securonix | Security Analytics Technology |
| 172 | Above Security | Managed Security Services Provider |
| 173 | Rohde & Shwarz | Encryption & IT Security |
| 174 | Secunia | Vulernability & Patch Management |
| 175 | Siemens Government Technologies | Cybersecurity for Federal Government |
| 176 | Osirium | Privileged User Management |
| 177 | SECNOLOGY | Log Analysis Software |
| 178 | SecureAuth | Secure Access Control |
| 179 | Adallom | Cloud & SaaS Security |
| 180 | StrongAuth | Enterprise Key Management Infrastructure |
| 181 | TeleSign | Mobile Identity Verification |
| 182 | Sumo Logic | Big Data Security Analytics |
| 183 | Juniper Networks | Threat Intelligence & Network Security |
| 184 | SecureKey | Identity & Authentication Solutions |
| 185 | Hortonworks | Big Data Security Analytics |
| 186 | SilverSky | Security-as-a-Service |
| 187 | SDS | Multi-Platform Encryption |
| 188 | NetScout | Situational Awareness & Incident Response |
| 189 | Syntegrity Networks | Identity Management & Data Security |
| 190 | Syncplicity | Secure File Storage |
| 191 | Easy Solutions | Electronic Fraud Protection |
| 192 | ThreatSim | Proactive Phishing Defense |
| 193 | MeasuredRisk | Cyber Advisory & Risk Analysis |
| 194 | Brainloop | Secure Document Management |
| 195 | Innové | Managed Security Services |
| 196 | TrulyProtect | Software Application Protection |
| 197 | Swivel Secure | Risk Based Authentication |
| 198 | ENCODE | IT Security & Digital Risk Management |
| 199 | TrapX Security | Threat Detection & Prevention |
| 200 | SpectorSoft | Threat Early Warning System |
| 201 | Sonatype | Enterprise Application Security |
| 202 | Skycure | Mobile Device Protection |
| 203 | ERPScan | SAP Security Solutions |
| 204 | Aegify | Security, Risk & Compliance |
| 205 | Antiy Labs | Anti-Virus Engine & Solution |
| 206 | Pwnie Express | Network Security Risk Assessment |
| 207 | Redhawk Network Security | Managed Security & Consulting Services |
| 208 | Centripetal | Cyber Threat Intelligence |
| 209 | Okta | Enterprise Identity Management |
| 210 | Ping Identity | Identity & Access Management Platform |
| 211 | Qosmos | Real-Time Data Security |
| 212 | OPSWAT | IT Infrastructure Security & Management |
| 213 | 21CT | Security Analytics & Visualization |
| 214 | Recorded Future | Real-Time Threat Intelligence |
| 215 | Cigital | Application Security Testing |
| 216 | CipherCloud | Cloud Visibility & Data Protection |
| 217 | Wave Systems | Software for Hardware-Based Security |
| 218 | Outlier Security | Endpoint Threat Detection & Response |
| 219 | Digital Shadows | Cyber Intelligence Feeds |
| 220 | Fluke Networks | Wireless Intrusion Prevention |
| 221 | Modulo | IT Governance, Risk & Compliance |
| 222 | Ridge-Schmidt Cyber | Executive Cyber Solutions |
| 223 | Paraben | Digital Forensics & Data Recovery |
| 224 | MindPoint Group | IT Security Solutions |
| 225 | F-Secure | Internet Security for All Devices |
| 226 | The Chertoff Group | Global Risk Management |
| 227 | Ntrepid | Secure Network & Online Computing |
| 228 | Mycroft | Identity & Access Management |
| 229 | Onapsis | ERP Cybersecurity Solutions |
| 230 | PrivateCore | Malware Detection & Prevention |
| 231 | QuintessenceLabs | Data Security Technology |
| 232 | PrimeKey Solutions | PKI & Digital Signature Solutions |
| 233 | RedSeal | Cybersecurity Analytics |
| 234 | Solutionary / NTT | Managed Security Services Provider |
| 235 | Oberthur Technologies | Digital Security for Mobility |
| 236 | VU Security | Identity Security & Fraud Prevention |
| 237 | Definisec | Endpoint Data Protection |
| 238 | Coverity | Software Testing & Security |
| 239 | GreyCastle Security | Information Security Consulting |
| 240 | EastWind Networks | Breach Detection |
| 241 | Prevalent Networks | Third-Party Risk Management |
| 242 | Avatier | Identity Management |
| 243 | Metova | Cyber Attack Management |
| 244 | Hexadite | Cyber Incident Response |
| 245 | OneLogin | Enterprise Identity Management |
| 246 | Forum Systems | Secure Cloud Gateway |
| 247 | Radiant Logic | Enterprise Identity Management |
| 248 | Reservoir Labs | Real-Time Threat Visibility |
| 249 | Radware | Application Security & Delivery |
| 250 | Smoothwall | Unified Threat Management |
| 251 | MetricStream | IT Governance, Risk & Compliance |
| 252 | Lynx Software Technologies | Real Time Threat Detection |
| 253 | LogRhythm | Log Management & Security Analytics |
| 254 | AlgoSec | Security Policy Management |
| 255 | Google Cloud Security Scanner | |
| 256 | ThreatStream | Cyber Threat Defense |
| 257 | SailPoint | Identity & Access Management |
| 258 | Becrypt | Mobile Device & Data Security |
| 259 | Gigamon | Data Center & Cloud Security |
| 260 | FoxT | Network Security & Assess Management |
| 261 | Praetorian | Cybersecurity Consulting & Services |
| 262 | LANDesk | Enterprise Endpoint Security |
| 263 | SENTRIX | Web Application Security |
| 264 | Monterey Technology Group | Microsoft Product Security |
| 265 | ManageEngine | Firewall & Log Management |
| 266 | White Ops | Bot Fraud Detection & Prevention |
| 267 | Microsoft | Windows Anti-Virus Protection |
| 268 | LockPath | IT Governance, Risk & Compliance |
| 269 | CACI | Intelligence, Defense & Federal Security |
| 270 | Wetstone Technologies | Cybercrime Investigations & Digital Forensics |
| 271 | Identity Finder | Data Discovery & Protection |
| 272 | HID Global | Secure Identity Technology |
| 273 | Guardian Analytics | Behavioral Analytics for Fraud Prevention |
| 274 | Red Canary | Threat Detection & Response |
| 275 | InfoExpress | Endpoint Security & Management |
| 276 | Keypasco | Multi-Factor Authentication |
| 277 | Kroll | Cybersecurity Services |
| 278 | FireMon | Network Security Management |
| 279 | HyTrust | Cloud Security Automation |
| 280 | Infocyte | Intrusion Assessment Platform |
| 281 | General Dynamics | IT Cybersecurity Solutions |
| 282 | MCSI | Enterprise Incident Response |
| 283 | iboss | APT Defense, Web & Mobile Security |
| 284 | IronKey | Hardware Encrypted USB Drives |
| 285 | Klocwork | Source Code Analysis |
| 286 | Lieberman Software | Privileged Identity Management |
| 287 | Lumension Security | Endpoint Management & Security |
| 288 | Malcovery Security | Threat Intelligence & Forensic Analysis |
| 289 | Mimecast | Microsoft Exchange Email Security |
| 290 | MicroStrategy | Mobile Identity Platform |
| 291 | Infoblox | Automated Network Control & Security |
| 292 | Messageware | Microsoft Exchange Security |
| 293 | Hexis | Malware Detection & Protection |
| 294 | Untangle | Network Security Appliance |
| 295 | Futurex | Hardened Enterprise Security Cloud |
| 296 | Glimmerglass | Cyber Terrorism & Fraud Prevention |
| 297 | Marble Security | Mobile Threat Intelligence |
| 298 | GreenSQL | Database Security & Compliance |
| 299 | GuruCul | Security Risk Intelligence |
| 300 | GlobalSign | Authentication & Identity Service Provider |
| 301 | Acuity Risk Management | IT Governance, RIsk & Compliance |
| 302 | Denim Group | Secure Software Development Services |
| 303 | Solarwinds | IT Security Software |
| 304 | Cyber Security Canada | Cybersecurity Services for SMBs |
| 305 | Link11 | DDoS Mitigation Solution Provider |
| 306 | Interset | Threat Detection & Prevention |
| 307 | Duo Security | Cloud Based Two-Factor Authentication |
| 308 | Allegro Software | Embedded Device Security |
| 309 | ESET | Multi-Device End Point Security |
| 310 | F5 | Cloud & Data Center Security |
| 311 | Darktrace | Cyber Threat Prevention |
| 312 | Daon | Identity Assurance & Biometrics |
| 313 | Cylance | Cyber Threat Intelligence |
| 314 | Avecto | Endpoint Security Software |
| 315 | Panda Security | Anti-Virus & Internet Security Software |
| 316 | Protected Networks | Identity & Access Rights Management |
| 317 | DeviceLock | Endpoint Data Leak Prevention |
| 318 | Entersekt | Authentication & Fraud Protection for Banks |
| 319 | Fasoo | Data & Software Security |
| 320 | eSentire | Threat Detection & Prevention |
| 321 | CloudFlare | Web Performance & Security |
| 322 | vArmour | Data Center Security |
| 323 | Bitglass | Data Protection & Breach Discovery |
| 324 | Vectra Networks | Cyber-Attack Detection & Management |
| 325 | Druva | Endpoint Data Protection & Governance |
| 326 | Lookout | Mobile Security for Android & iOS Apps |
| 327 | Triumfant | Endpont Security & Malware Detection |
| 328 | GuardiCore | Data Center Security |
| 329 | lastline | Security Breach Detection |
| 330 | Delta ID | Secure Biometric Authentication |
| 331 | Vistronix | Cybersecurity for Federal Agencies |
| 332 | PixAlert | IT Governance, Risk & Compliance |
| 333 | Cyactive | Malware Detection & Protection |
| 334 | Agari | Real-Time Cyberthreat Detection |
| 335 | Zenedge | Web Application Security |
| 336 | Absolute Software | Mobile Device Management & Security |
| 337 | Prelert | Machine Learning Anomaly Detection |
| 338 | Risk I/O | Vulnerability Threat Management |
| 339 | Secure Access Technologies | Mobile Single Sign-On |
| 340 | WhiteHat Security | Web Application Security |
| 341 | Sungard AS | Managed Security Services |
| 342 | Virtual Forge | SAP Application Security |
| 343 | StillSecure | Network Access Control |
| 344 | Secure Decisions | Security Visualization for Cyber Defense |
| 345 | Hillstone Networks | Data Analytics Firewall Protection |
| 346 | ForgeRock | Open Source Identity Management |
| 347 | Code42 | Data Management & Protection |
| 348 | N-Stalker | Web Application Security Scanner |
| 349 | GFI | Email & Network Security Solutions |
| 350 | Acunetix | Web Vulnerability Scanner |
| 351 | AirTight | Wireless Intrustion Prevention System |
| 352 | Accellion | Secure Mobile File Sharing |
| 353 | InteliSecure | Network Security Services |
| 354 | PortSwigger | Web Application Security Testing |
| 355 | Sword & Shield | Managed Security Services |
| 356 | EdgeWave | Military Grade Internet Security |
| 357 | Contrast Security | Application Security Software |
| 358 | Wandera | Secure Mobile Gateway |
| 359 | XBridge | Mainframe Data Loss Prevention |
| 360 | DeepNines | Network Security Solutions |
| 361 | Sqrrl | Cyber Defense Analytics |
| 362 | ContentKeeper | Malware Detection & Prevention |
| 363 | WatchGuard | Threat Management Appliances |
| 364 | OnWire | IBM Security Product Integration |
| 365 | AllClear ID | Identity Protection Service |
| 366 | Defense Point Security | Cybersecurity Services for Federal Agencies |
| 367 | Wontok | Anti-Fraud Technology |
| 368 | Good | Secure Mobility Solution |
| 369 | Gigya | Customer Identity Management |
| 370 | BAE Systems | Cybersecurity Risk Management |
| 371 | Patriot | Mobile Device Security Management |
| 372 | KEYW | Cyber Defense & Digital Forensics |
| 373 | ID Experts | Healthcare Fraud & Identity Protection |
| 374 | CSC | IT Security Services |
| 375 | RiskSense | Malware Detection & Protection |
| 376 | InfoGard | IT Security Assurance Services |
| 377 | AnchorFree | End-to-End Information Security |
| 378 | WatchDox | Secure Document Management |
| 379 | INSIDE Secure | Smartphone & Mobile Device Security |
| 380 | Eid Passport | High-Assurance Identity Management |
| 381 | SecureLogix | UC Security & Management |
| 382 | CloudPassage | Cloud Infrastructure Security |
| 383 | Tevora | IT Governance, Risk & Compliance |
| 384 | Aspect Security | Application Security Consulting |
| 385 | Quotium | Application Security Testing & Protection |
| 386 | Red Lambda | Big Data Security Analytics |
| 387 | Light Cyber | Active Breach Detection |
| 388 | Privacy Analytics | Healthcare Data Privacy |
| 389 | Promisec | Endpoint Security Intelligence |
| 390 | RSD | Information Governance Solutions |
| 391 | Sypris | Encryption & Biometric Solutions |
| 392 | Saint Corporation | IT Security Risk & Compliance |
| 393 | Exabeam | User Behavior Intelligence |
| 394 | TeraDact | Secure Information Sharing |
| 395 | TRUSTe | Data Privacy Management |
| 396 | Barracuda Networks | Email & Web Security Appliances |
| 397 | WildPackets | Cyber Attack Analysis |
| 398 | DATASHIELD | Data Security Services |
| 399 | Evident.io | Cloud Security Platform |
| 400 | NT OBJECTives | Web Application Security |
| 401 | CrowdStrike | Endpoint Protection & Threat Intelligence |
| 402 | Synack | Crowd Security Intelligence |
| 403 | Endgame | Security Intelligence & Analytics |
| 404 | Clef | Two-Factor Authentication |
| 405 | TargetProof | Identity Verification & Fraud Prevention |
| 406 | Skybox Security | Risk Analytics for Cybersecurity |
| 407 | Waterfall | Cybersecurity for NERC-CIP Compliance |
| 408 | Syferlock | Software-based Authentication |
| 409 | NexDefense | Automation & Control Systems Security |
| 410 | Nok Nok Labs | Unified Authentication Infrastructure |
| 411 | Area 1 Security | Cyber Threat Intelligence |
| 412 | Vkansee | Fingerprint Sensors for Mobile Security |
| 413 | Secure Digital Solutions | Infosecurity Consulting Services |
| 414 | Ionic Security | Data Privacy & Protection |
| 415 | AnubisNetworks | Threat Intelligence & Email Security |
| 416 | Ixia | Network Visibility, Security & Testing |
| 417 | Virtru | Secure Email & Digital Privacy |
| 418 | Grid32 Security | Cybersecurity Consulting Services |
| 419 | LaunchKey | Mobile Authentication Platform |
| 420 | 405Labs | Data Loss Prevention |
| 421 | SentinelOne | Endpoint Protection Platform |
| 422 | Dataguise | Big Data Security |
| 423 | VisiTrend | Cybersecurity Analytics |
| 424 | Penango | Email Encryption & Security |
| 425 | Forensic Innovations | Data Discovery & Forensics |
| 426 | pixlcloud | Security Analytics & Visualization |
| 427 | ForeScout | Network Security & Access Control |
| 428 | PacketSled | Threat Detection & Network Forensics |
| 429 | Blueliv | Cyber Threat Analysis |
| 430 | Crypteia Networks | Managed Security Services |
| 431 | Kryptnostic | Encrypted Search SDK |
| 432 | Damballa | Automated Breach Defense |
| 433 | Proteus Security | Information Security Services |
| 434 | Taia Global | Cybersecurity Consulting Services |
| 435 | 6Scan | Website Security & Malware Quarantine |
| 436 | Farsight Security | Actionable Threat Intelligence |
| 437 | Mocana | Mobile & Internet of Things Security |
| 438 | AXON Ghost Sentinel | Internet of Things Security |
| 439 | Avast | Anti-Virus Protection for MACs |
| 440 | Hyperion Gray | Open Source Web Security |
| 441 | RedOwl | Data Analytics for Risk & Compliance |
| 442 | G2 Ops | Cybersecurity Architectural Analysis |
| 443 | Cienaga Systems | Cyber Threat Management |
| 444 | SecSign | Mobile ID Authentication |
| 445 | Sensato | Healthcare IT Security & Privacy |
| 446 | Veris Group | Cybersecurity Professional Services |
| 447 | CenturyLink | Multi-Layered Network Security |
| 448 | VEEDog | Malware Detection Appliance |
| 449 | Vidder | Cyber Attack Prevention |
| 450 | Security Compass | Software Development Security |
| 451 | ThreatConnect | Cyber Threat Intelligence Platform |
| 452 | PhishLabs | Cybercrime Detection & Prevention |
| 453 | Oxford Biochronometrics | Online Fraud Detection & Prevention |
| 454 | Bugcrowd | Crowd Sourced Security Testing |
| 455 | Security Innovation | Application Risk Management |
| 456 | Defence Intelligence | Real-Time Malware Protection |
| 457 | AlphaGuardian | Cyber Safe Infrastructure |
| 458 | GhostMail | Free Encrypted Email & Chat |
| 459 | Mosaic 451 | Cyber Security Services |
| 460 | Seclytics | Security Analytics & Threat Intelligence |
| 461 | GuidePoint Security | Information Security Services |
| 462 | Vanguard Integrity Professionals | Cybersecurity Consulting & Training |
| 463 | Groundworks Technologies | OS & Embedded Devices Security |
| 464 | Auconet | Network Visibility & Security |
| 465 | Risk Based Security | Cyber Risk Analytics |
| 466 | Mobile Active Defense | Mobile Device Protection |
| 467 | Citicus | Risk & Compliance Management |
| 468 | SAS Cybersecurity | Fraud & Security Intelligence |
| 469 | SurfWatch Labs | Cyber Risk Intelligence Analytics |
| 470 | Netskope | Cloud Application Security |
| 471 | Light Point Security | Web Safety & Malware Protection |
| 472 | PUNCH | Cyber Threat Advisory & Consulting |
| 473 | CoSoSys | Data Loss Prevention |
| 474 | Fulcrum Biometrics | Biometric Identification Systems |
| 475 | Selex ES | Cybersecurity & Information Assurance |
| 476 | Harris | Cybersecurity for Federal Agencies |
| 477 | Comodo | IT Security Management |
| 478 | Paladion | Cybersecurity Testing & Monitoring |
| 479 | Sirrix AG | IT Security Consultants & Cryptographers |
| 480 | Cryptomathic | Cloud, Mobile & Network Security |
| 481 | AlertEnterprise | Physical Identity & Access Management |
| 482 | nwStor | Network & Cloud Data Security |
| 483 | Distil Networks | Malicious Bot Detection & Prevention |
| 484 | Apperion | Mobile App Security |
| 485 | CounterTack | Real Time Attack Intelligence |
| 486 | WinMagic | Full-Disk Encryption Software |
| 487 | Protectimus | Two Factor Authentication |
| 488 | Tempered Networks | Network Security |
| 489 | Celestix | Authentication & Perimeter Security |
| 490 | Cato Networks | Cloud Network Security |
| 491 | Seclore | Secure File Sharing |
| 492 | GrammaTech | Software Code Security |
| 493 | Bluebox Security | Mobile App Security |
| 494 | Deja vu Security | Infosecurity Consulting & Research Services |
| 495 | CloudHASH Security | Enterprise Endpoint Security |
| 496 | Aujas | Information Risk Management Services |
| 497 | Fortscale | Big Data Cyber Analytics |
| 498 | NetFort | Network Security Monitoring |
| 499 | Citrix | Secure Remote Access |
| 500 | Imprivata | Security for Healthcare Providers |
完整的 Cybersecurity 500 请点 这里 查阅。转载请写明来自“游侠安全网”。
感谢“金湘宇(NUKE)”的提醒,这个榜单应该是“创新”500强。这个也是和主办方此前的解释一致的,按照销售额排名的话,可能远不是这样子。